
|
|
How to Use a USB Flash Drive and VeraCrypt to Maximize Privacy For Your Favorite Browser Without the Annoyance of Incognito/Private Mode |
This is a pre-publication, incomplete version for some friends. There are some holes and incomplete thoughts here. Use at your own risk.
The approach described here will permit you to run many programs and keep the associated data from those programs on an encrypted USB flash drive. The instructions provided here make this all very easy to do. You can remove the flash drive to hide and/or take to another computer. Primary candidates for such use are browsers like Chrome, Firefox, or Opera. These are all available in portable versions that can be put on a USB Flash Drive. That includes their associated cookies and other caches.
While these browsers all have private instance options, (e.g., new incognito window in Chrome), the use of these is problematic. They erase all new cookies and cached files when closed and may not allow one to install new plug-ins, extensions, or favorites. You also cannot review your browsing history, which is sometimes very useful. By putting a portable version of your browser onto an encrypted USB flash drive, all this data remains very secure and so you do not need to use the incognito/private mode. You can use the normal mode and rest easier knowing that it would be almost impossible for anyone with access to your computer to determine the sites you have been visiting and files you have downloaded, unless you provide the right password.
If you are not concerned about using a USB flash drive (so you can remove it to either hide it or take it to another computer), then you can still follow these instructions, except put the VeraCrypt volumes (explained below) on a hard disk or SSD for better performance.
Before starting the cookbook approach below, you should skim through it once, including the section Variations at the end. Then come back here to begin. Be certain to read the Caveats section as well, especially the need for a virtual private network (VPN) server. The VeraCrypt volume will only protect local data, not data that travels out of your computer, so you will need a VPN server and several other measures described below for more privacy.
|
|
NOTE: Nothing here is intended to help you get away with breaking any US laws. Although I believe that all significant browsing artifacts on your personal machine can be hidden by these techniques, nothing is guaranteed. Use at your own risk. In addition, the article suggests some techniques to significantly lower your risk of exposing your identity to the Internet, but there are too many ways for this to happen to cover here; in fact, that may be impossible. If you are a dissident in a repressive country and want to visit prohibited sites, the techniques here will not adequately help you. |
|
Create the folder C:\ZDrive. This is a temporary folder that you will later copy to two VeraCrypt volumes and then delete. C:\ZDrive is so named because the VeraCrypt volumes will ultimately be mounted to Z: (in this article).
Install the PortableApps Platform to C:\ZDrive. You can do this even if you already have a PortableApps Platform installed elsewhere.
Once installed, click Apps -> Get More Apps -> By Category. Check off VeraCryptPortable, a browser, and anything else you think might be handy (KeePass?). For the rest of the article, let's assume you picked Google Chrome because that is what you have been using.
The ChromePortable you will soon be using will almost certainly ask if you want to make it your default browser. You do not want this because it will make an entry in the registry pointing to your VeraCrypt volumes. Google does not make it easy to override this annoyance, but overriding it is only a simple registry setting. Just click the following link and download to any folder. Then in a file explorer, right click the reg file and select Merge or Run: StopChromeAskingToBeDefault.reg. If you want to see the contents first or you want to do it manually, just see this link: https://www.rtbaileyphd.com/src/tools/StopChromeAskingToBeDefault.reg.
Run Chrome from the PortableAppsPlatform menu to create your initial profile. Then use the file explorer to look at C:\ZDrive\PortableApps\GoogleChromePortable\Data\profile. This is where the various caches with cookies, sites visited, etc. are stored. With one exception (details below), these caches are not stored elsewhere; that is what makes this Chrome portable, and that is what makes the approach described below feasible. You probably noticed that your ChromePortable was fresh; i.e., it showed none of the bookmarks or extensions in your standard Chrome. This will be fixed below. Close ChromePortable now so this fix can be done.
As just explained, there is an exception that PortableApps programs keep all their data within the PortableApps folder. Some programs, Chrome included, will use a system temporary folder (%TEMP% or %TMP%). These two environment variables need to be reset before any PortableApps program is started. This can be accomplished by starting the PortableAppsPlatform using a simple batch script that sets %TEMP% and %TMP% to the TEMPDIR folder within C:\ZDrive or inside the two VeraCrypt volumes to which it will be copied. Click the following link and save the script to C:\ZDrive: START_PORTABLEAPPS.bat. If you want to see the file contents first, just click rtbaileyphd.com/src/tools/START_PORTABLEAPPS.bat
To avoid confusion, delete C:\ZDrive\Start.exe and C:\ZDrive\Autorun.inf since you should always start PortableApps using Z:\START_PORTABLEAPPS.bat. When you click C:\ZDrive\START_PORTABLEAPPS.bat, you will see the PortableAppsPlatform GUI, which looks something like this:
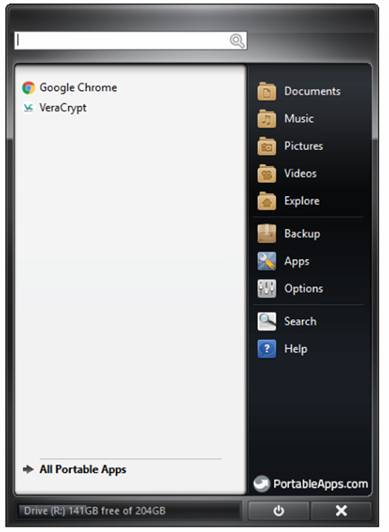
Always start Chrome from here. Never start Chrome from Z:\PortableApps\GoogleChromePortable\GoogleChromePortable.exe. If you do the latter, then the temp files will not be put in your hidden folder Z:\TEMPDIR, and will leak out to an unprotected drive.
In the PortableAppsPlatform Options, make certain that "Close Apps on Platform Exit" is checked:
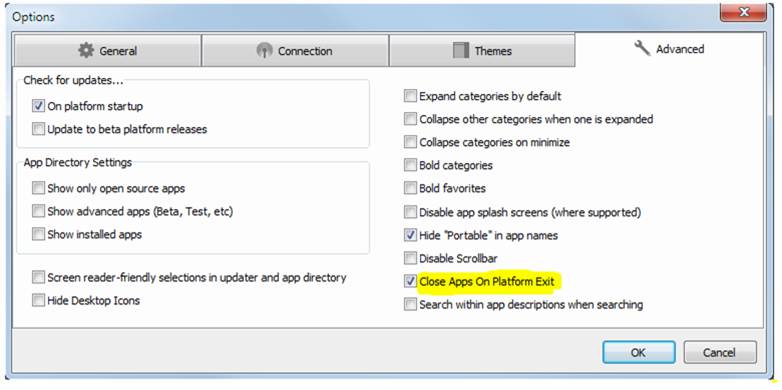
If you fail to do that, your Z:\TEMPDIR will not be cleaned up properly.
Do not clean the cache of your standard Chrome. You want an installation with a typical cache, not a clean one. However, do clean your cache if there is something you definitely do not want others to ever see.
Close ChromePortable and also close your standard Chrome. Now delete
C:\ZDrive\PortableApps\GoogleChromePortable\Data\profile
Copy
"C:\Users\<your username>\AppData\Local\Google\Chrome\User Data" to
C:\ZDrive\PortableApps\GoogleChromePortable\Data\
Now rename
"C:\ZDrive\PortableApps\GoogleChromePortable\Data\User Data" as
C:\ZDrive\PortableApps\GoogleChromePortable\Data\profile
Now restart ChromePortable. You should see it looking like your old standard Chrome.
The process is essentially the same for other browsers. The locations of your profile/settings will differ however. Google something like "how do I move all my Firefox settings to another computer".
You may see that you are logged in to your Google account, if you have one. You do not want that for your ChromePortable. In your ChromePortable go to google.com and sign out by clicking your icon in the upper right. In addition go to chrome://settings and make certain you are signed out there as well. Remain in the chrome://settings page.
Scroll down to Themes. Select a theme that is much different than your current one. This is to help you avoid confusion in case you alternate between your old Chrome and your new encrypted Chrome.
Continue scrolling to Search Engine. Select a private one like https://www.startpage.com/. This actually uses google.com, but via a proxy so Google will not know who submitted the search or from where it came. Duckduckgo.com is also popular, but the results are not as good as StartPage.
Scroll down to Advanced and click that to open up more choices.
Go to chrome://extensions. Some extensions will send sensitive information to sites on the Internet. For certain, any antivirus extensions for "Safe Surfing" will do that. To see just how bad it is, see the table on page 3 of http://www.av-comparatives.org/wp-content/uploads/2014/04/avc_datasending_2014_en.pdf, especially the lines "Is a unique identification number transmitted?" and "Are visited URLs transmitted?". Another one you certainly need to eliminate is "Web of Trust"; see http://www.pcworld.com/article/3139814/software/web-of-trust-browser-extensions-yanked-after-proving-untrustworthy.html. Another is Ghostery; see https://www.technologyreview.com/s/516156/a-popular-ad-blocker-also-helps-the-ad-industry/. For a good general discussion, see howtogeek.com/188346/why-browser-extensions-can-be-dangerous-and-how-to-protect-yourself/. The key message here is that you should eliminate as many extensions as you can, unless they serve to enhance your privacy. But, then, how do you know if the extensions you have left are tracking you? For a general guide, see ghacks.net/2015/11/21/verify-google-chrome-extensions-before-you-install-them/.
TBD: https://multiloginapp.com/
See also https://www.howtogeek.com/100361/how-to-optimize-google-chrome-for-maximum-privacy/.
TBD Fingerprinting: https://browserleaks.com/ https://panopticlick.eff.org/ https://www.maxa-tools.com/cookie-privacy.php http://www.networkworld.com/article/2884026/security0/browser-fingerprints-and-why-they-are-so-hard-to-erase.html https://amiunique.org/ Can find extensions even if blockers are turned on: https://extensions.inrialpes.fr/
Now browse to a few sites in ChromePortable that would make you somewhat embarrassed about if caught. Let's say you browsed to http://cowudders.com because you like looking at cow udders but don't want anybody knowing about it. Of course do not visit anything yet that would be illegal in your country, just sufficiently embarrassing to create a good cover story.
Insert your flash drive. Let's say it is assigned to drive J:. You are going to be creating a file larger than 4 GB. Files that large are not supported by a FAT32 file system, which is most likely what your flash drive is. So it must be changed to an NTFS type. If there are important files on you flash drive already, then copy them to a temporary place on another drive so they do not get lost. Then just enter these two commands in a command prompt window:
chkdsk J:
convert J: /fs:ntfs
If any preexisting file on J: is damaged or missing, restore it from the backup you just made.
Copy C:\ZDrive\PortableApps\VeraCryptPortable to J:\VeraCryptPortable. You will need a copy of VeraCryptPortable on your flash drive to use your flash drive on another computer. You do not need to copy anything else yet.
You are going to create a VeraCrypt volume named PrivateBrowser on your J: flash drive and map the VeraCrypt volume to the Z: drive. Do not try to be secretive at this point; the camouflage part comes later when you will create a hidden inner volume within PrivateBrowser.
Open VeraCrypt and select "Volumes/Create new volume" from the menu. Then you will see this:
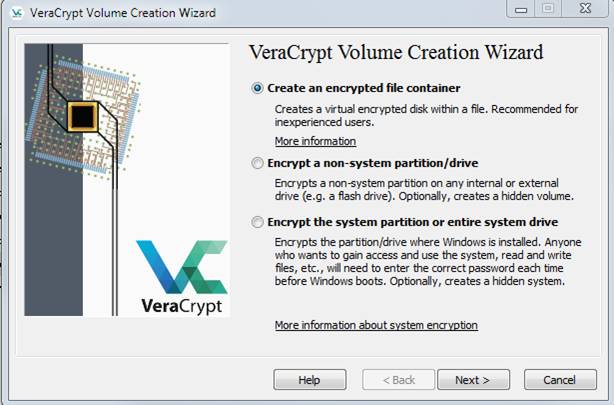
Just click Next since a file container is sufficient. On the next dialog, select Hidden VeraCrypt volume, like this:
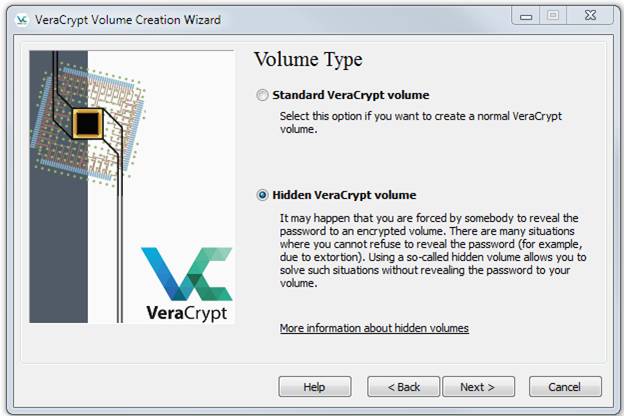
Click Next. Then you will see this:
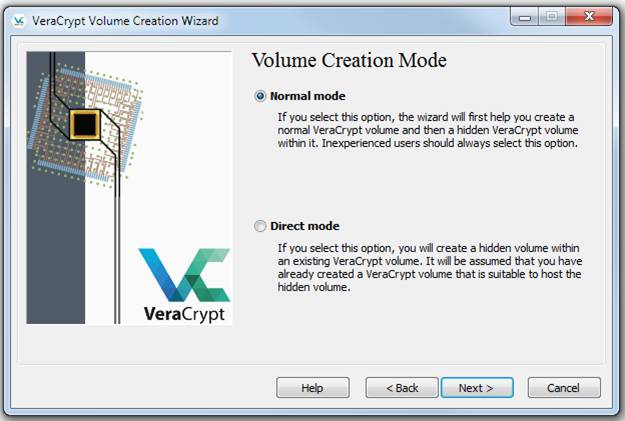
Just leave Normal mode selected and click Next. On the next dialog, enter J:\PrivateBrowser in the Volume Location box:
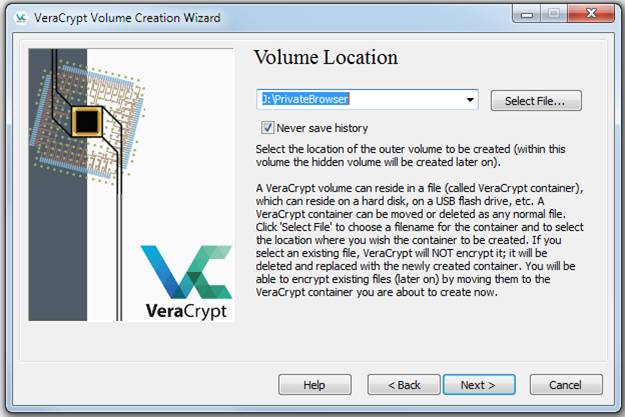
Click Next three times, which will get you to the Outer Volume Size dialog. Specify a generous amount of space, but, since formatting your volume takes quite a bit of time, do not get carried away:
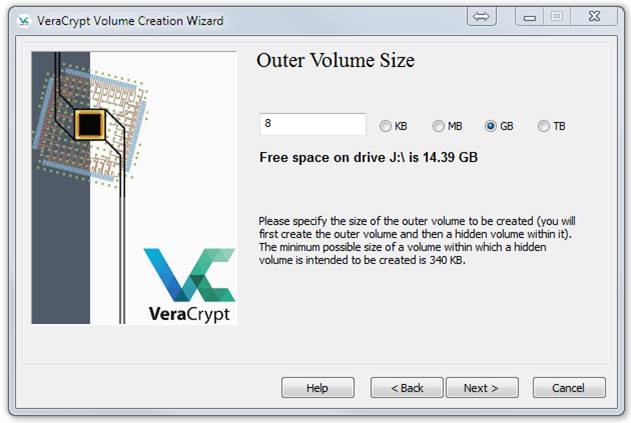
Click Next and then you will see this:
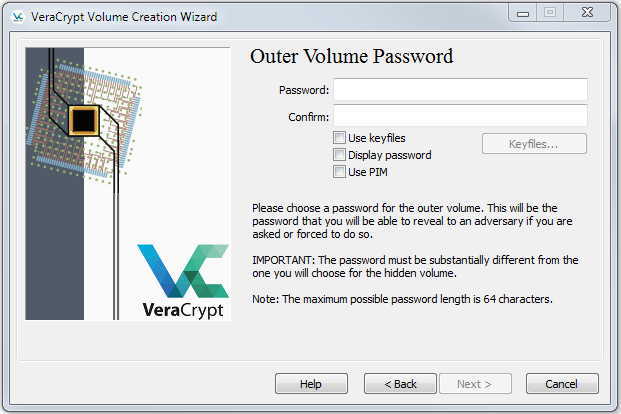
Enter a fairly long password, but something you can easily recall. Remember that you might not be able to look at your password manager if you are trying to use your flash drive on another machine. This password will just provide access to the decoy files that will be put in your volume, so you only need to make it plausibly secure. Enter the password and click Next to see:
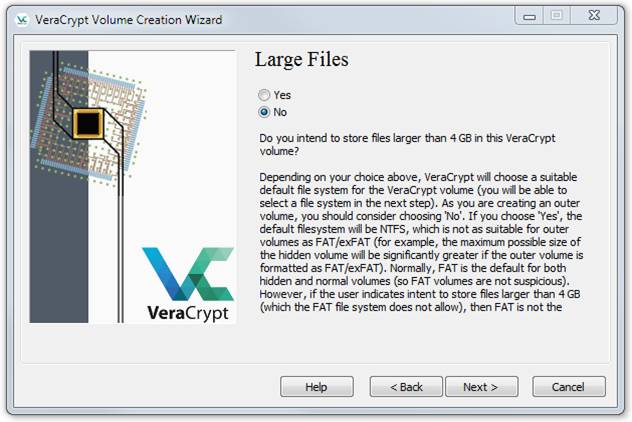
Leave No selected and click Next to see:

You need to move your mouse randomly over this dialog until the Randomness bar is all green. Then click Format. The formatting may take quite a few minutes. For the example above it took 18 min to complete via USB 3 (blue tab), including 2 min after the Left box said 0. The VeraCrypt time left estimator significantly underestimates the time left. After that you will see something like this:
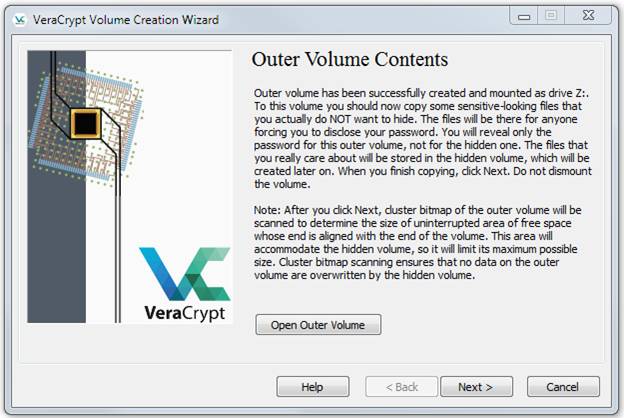
Do not follow the instructions in the dialog box above. When we followed those instructions, the version we ran did not calculate the used space correctly and only allowed us a very small amount of space for the inner (hidden) volume. Instead, just click Next three times to get to this:
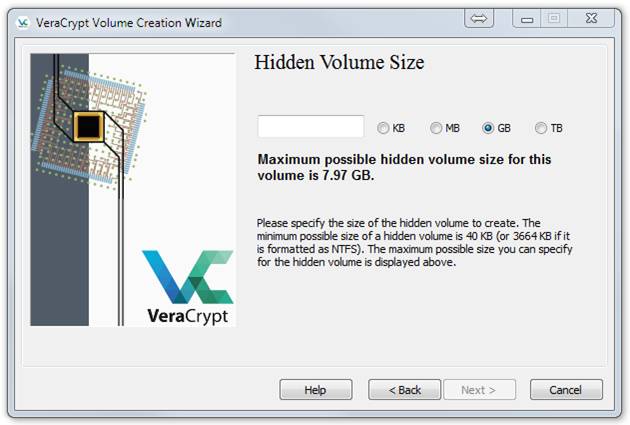
Before choosing, you need to check how much space the outer volume will require. In File Explorer, right click on C:\ZDrive and select Properties. That will show you how much space that your outer volume will require for your decoy browser installation. In our case we saw this:
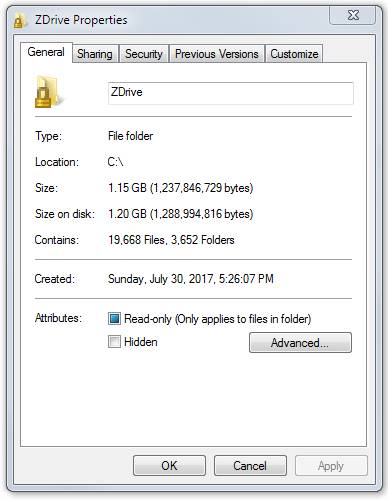
We could use up to 6.77 GB for the inner volume, but to allow some room for error, we chose to allocate just 6 GB. That allows room in the hidden volume for downloading some files or for adding other portable applications. After entering 6 GB and clicking Next, we saw this:
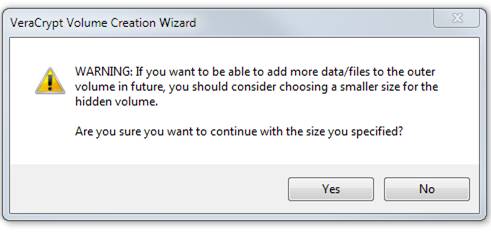
We intend to be careful and not use the outer volume and we have 770 MB extra there anyway, so we clicked Yes here. Then this:
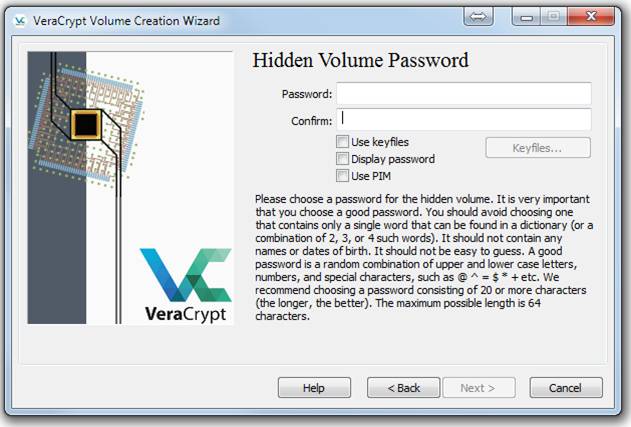
Enter your inner password. Make certain it is very much different from the outer password, and also more secure. Before you choose, you might want to Google this: how to choose memorable passphrases. Click Next to see this:
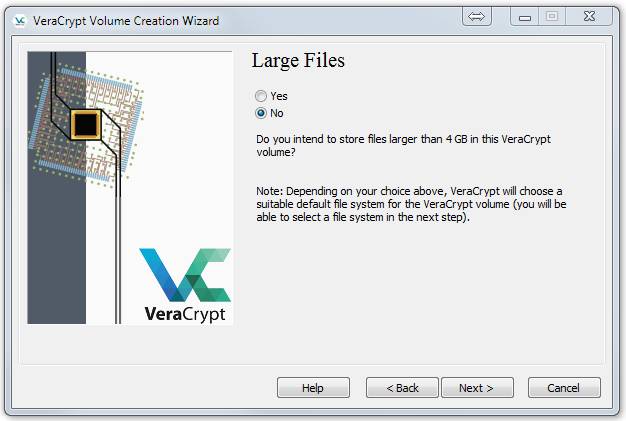
Leave No selected and then click Next. Then you will see this:
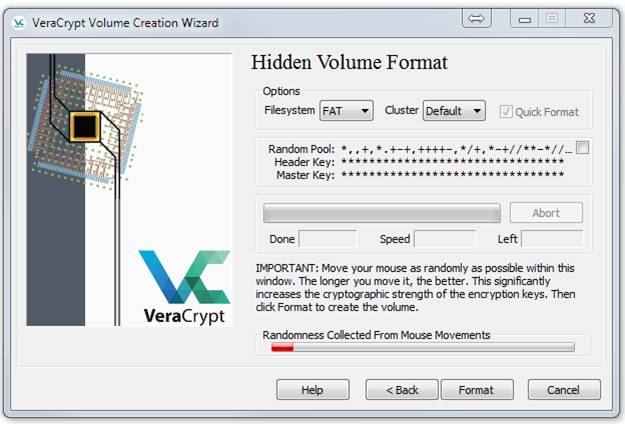
Move your mouse over the dialog box until the Randomness bar is all green. Then click Format. This formatting will not take long. Then you will see this:
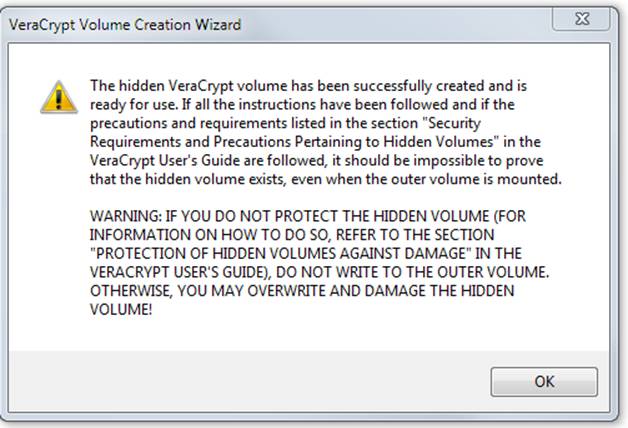
Read the above dialog box carefully. Click OK and then click Exit on the next dialog. You will then see the VeraCrypt main dialog. Enter J:\PrivateBrowser in the file entry box and select a drive to which it is to be mounted from the drive list. You should then see something like this:
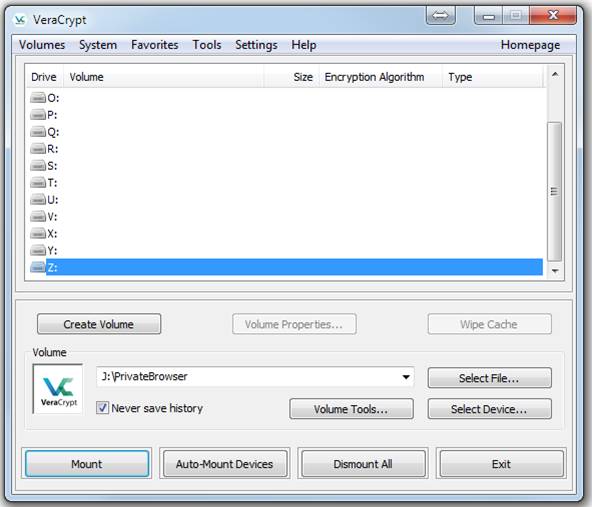
Now click Mount to show this:
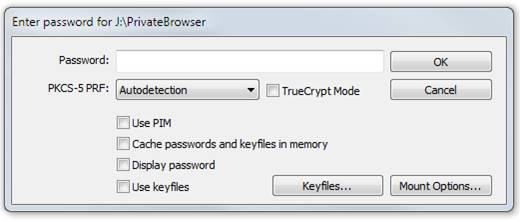
We will fill the hidden inner volume first, so enter your inner password and click OK. You will then see this:
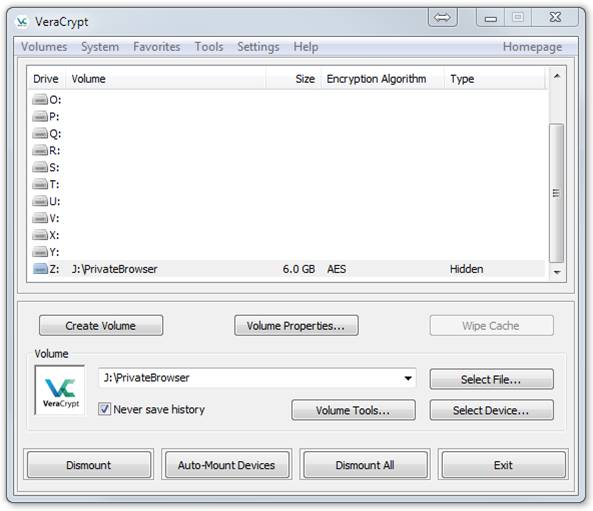
Note that the size of the hidden volume is shown and also its type (Hidden). It is obvious from this that there is a hidden volume inside the outer volume. So when you are not actively using your hidden volume, it may be wise to Dismount it. Leave VeraCrypt running so you can Dismount Z: when done.
Now make certain your original portable browser in C:\ZDrive\... is closed, and then copy
file C:\ZDrive\START_PORTABLEAPPS.bat,
folder C:\ZDrive\Downloads,
folder C:\ZDrive\Documents, and
folder C:\ZDrive\PortableApps
to Z:\
This will take some time. In our example, it took 15 min for a USB 3 drive.
Now run Z:\START_PORTABLEAPPS.bat and when the PortableAppsPlatform opens, click Google Chrome. Then you might see this:
If you accept the offer to set Chrome as your default browser, you will create an entry in your registry pointing to
Z:\PortableApps\GoogleChromePortable\App\Chrome-bin\chrome.exe.
This will reveal that you have Chrome installed on a Z: drive. You probably not want that, so do not set it as the default, and adjust the settings to not ask again.
Open your Chrome settings. If you have a Google account, verify that you are not signed in.
At the bottom of Settings open the Advanced settings. Using the Make New Folder button, set the Downloads location to Z:\GoogleChromePortable\Downloads. Also make very certain to turn on (make blue) "Ask where to save each file before downloading". This is in case you are not able to mount to the Z: drive sometime in the future. You do not want to take the chance of saving something to somewhere else than your hidden VeraCrypt volume. Download something to test that you have set this up correctly. E.g., download the very small file ShortcutLauncher.pl from https://www.rtbaileyphd.com/download/ and verify it ended up in Z:\GoogleChromePortable\Downloads.
Under System make certain "Continue running background apps when Google Chrome is closed" is switched off.
Under Privacy and security -> Content settings -> Location turn off "Ask before accessing" so it says "Blocked". Note: this did not work for us. So also install a location faker extension such as "Manual Geolocation" and turn it on.
Optional: Near the top of settings under Appearance, select a different theme, probably from the minimalist section. The objective is to avoid confusion if you run Chrome from your unencrypted disk. It is a good idea to not run your public Chrome and your hidden Chrome at the same time. You do not want to accidently visit a site in your public Chrome that you intended to visit in your hidden Chrome.
Close the browser on your inner volume. Then Dismount Z:. You are likely to see this:
This always seems to happen. Just click Yes.
Now Mount Z: again. This time, however, enter your outer password. You should see something like this:
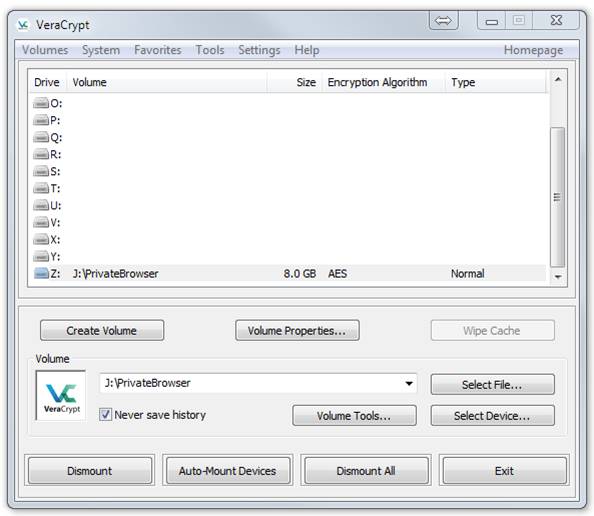
Note that the size is 8 GB, not 2 GB. This dialog will not reveal that there is a hidden volume inside your outer volume. In a File Explorer, right-click Z: and select properties. You should see something like this:
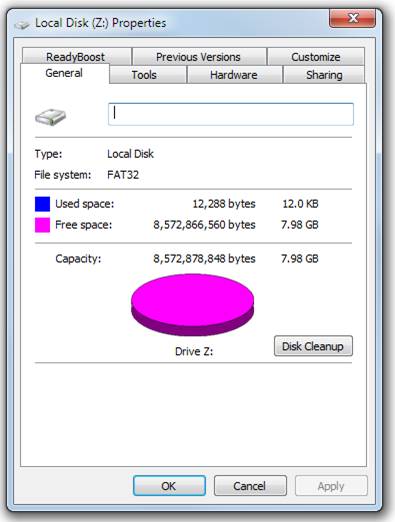
Again, there is no clue here about the hidden volume. Do not do anything to this volume such as defragging it. Just leave it alone, except for completing the setup.
To complete the setup, just follow the instructions above for setting up the inner volume, except you should probably use a different theme.
Close the browser on your outer volume, and close any File Explorers that have Z: opened. Then Dismount Z:. Click Yes to force a dismount, if needed.
Now click Mount in the VeraCrypt main dialog, and then enter the inner password. Verify that you see the Hidden volume under the Type column. Open your browser to verify that it is working OK. Look to see that all your extensions are active.
Close the browser and any File Explorers that have Z: opened. Then Dismount Z:. Click Yes to force a dismount, if needed. Remove the USB flash drive and take it to another computer. Test it there to make certain it works.
VeraCrypt on your USB Flash Drive. You were instructed to put it there for convenience in case you take your flash drive to another computer. However, having it there will make it obvious what type of file is PrivateBrowser. You could instead put VeraCrypt on a different flash drive and remember to take both with you, or you could install VeraCrypt on your flash drive after you get to the 2nd computer and then uninstall it when done.
Naming your VeraCrypt Volume PrivateBrowser. Perhaps that is too revealing. Name it something else and think of a cover story different than cowudders.com.
Google Account for your private browser. If you think you need a completely separate account, you will need to supply a phone number. You can get an anonymous number from smsprivacy.org
VPN service. The process described above will not protect your IP address from being collected by sites you visit or services you use. To prevent that, you will need a VPN service that specializes in privacy and specifically states that the service will not keep logs. Test your VPN using ipleak.net to see if it stops all 4 types of leaks (normal, DNS server, WebRTC, geolocation). You need to click the "Manual geolocation" button to check the latter. IPleak.net shows a location using the IP, but that is not the same as "Geolocation detection", so check both. If your location is revealed even though you have turned off location revealing in your browser, then install a location faker extension such as "Manual Geolocation" and try again.
Some VPN services do not support emailing from a local email client such as MS Outlook, so check that before signing up. Also check other services such as SSH.
Artifacts. The process described above will only protect some of the data that resides on your computer. Your private browser will leave artifacts in RAM and hence in your paging file (pagefile.sys). For Windows 8-10 there is also swapfile.sys. If hibernation is enabled, then hiberfil.sys will also include artifacts. These artifacts can reveal information about your activities. The RAM will be cleared by shutting down your machine. To clear the paging and swap files on shutdown you simple need to change one entry in your registry. See rtbaileyphd.com/src/tools/ClearPageFileAtShutdown.reg. To make the change easily, just click this link to download this reg file and then run/merge it: ClearPageFileAtShutdown.reg This registry setting will slow down your shutdown, and the files can still be examined prior to shutdown.
An alternative is to eliminate these files altogether. If you search the Internet, you will find that this is not advisable (and some who say you are simply stupid for thinking such thoughts), but you will find instructions on how to do it. See, for example, www.howtogeek.com/225143/what-is-swapfile.sys-and-how-do-you-delete-it/. However if you are, say, a dissident in Iran and you visit prohibited websites, you will not have a choice but to turn these files off. You are less likely to have problems if you have a lot of RAM. What you will need to do is to install a copy of Process Explorer (procexp.exe) from Microsoft at docs.microsoft.com/en-us/sysinternals/downloads/process-explorer. Then run your computer and open up procexp.exe and the programs you ordinarily use. Open up the maximum number of browser tabs you think you will need. Open up the procexp memory window by clicking the rectangular icon on the top. This is the one with the salmon color stripe. Then check if the Peak Commit Charge is less than 80% of the available Physical Memory. If so, then you can try eliminating pagefile.sys. Reboot your machine and you will see pagefile.sys and swapfile.sys are gone. Then run procexp.exe again and keep an eye on the Current/Limit number. If it gets to 90%, then close something. You can significantly reduce your Chrome memory usage by installing "The Great Suspender" and "XTab" extensions if you frequently get close to the 90% mark. 8 GB of RAM should allow you to safely run a browser, virus checker, messenger, procexp.exe, and several more programs.
To turn off hibernation, execute "powercfg.exe -h off" from a cmd window started using "Run as Administrator". Then you can delete C:\hiberfil.sys, and it should not come back.
Another artifact is your Domain Name Server (DNS) cache. Whenever your browser uses an address like www.somesite.com, it must first get the 4-part numeric address like 110.120.130.140 and then actually query the latter. It gets that number from your DNS. To help performance, Windows will put www.somesite.com and 110.120.130.140 into the DNS cache to avoid another query to your DNS. In reality it does not help much. This is because Chrome has its own internal cache. Type chrome://net-internals/#dns into the address bar to see it. That cache will reside on your hidden volume, so it is safe. So open a cmd window with "Run as Administrator" and flush the DNS cache with this: ipconfig /flushdns. Then enter services.msc. Scroll down to DNS Client and double click that line. Stop it by clicking Stop. Then for Startup type select Disabled. Then after rebooting try ipconfig /flushdns again. If you did everything right you should get an error message. It is beyond the scope of this paper to explain further, so see http://winhelp2002.mvps.org/hosts.htm.
As an aside, there is a big advantage to disabling your DNS cache; it allows you to add a large number of malicious or annoying sites to your hosts file If you have a large hosts file and the DNS cache service is running, your performance will be miserable. We have almost 40,000 entries on our computers, all managed automatically by the excellent application HostsMan, and all pointing to 0.0.0.0 (better than 127.0.0.1). HostsMan can automatically download the MVPS list as well as others whenever they change. With the right lists, you can speed up your browsing by not waiting for sites like adclick.g.doubleclick.net. Check chrome://net-internals/#dns to see how well HostsMan works. HostsMan can disable your DNS cache service for you.
Yet another type of artifact consists of certain registry keys, called "shellbags", that maintain folder usage information. This information can persist for years after the covered folders are deleted or their devices are removed from your system. As a result you should never create a folder anywhere whose name itself is revealing. Shellbags allow one to reopen the same folder at a later time with the settings from the previous time. For more info see www.ghacks.net/2014/06/09/remove-old-shellbag-entries-windows-privacy/. If you want to see what is on your computer, download and run privazer.com/download-shellbag-analyzer-shellbag-cleaner.php. That tool can also be used to remove shellbags. You could unmount your Z: drive and then tell the tool to remove all shellbags for missing folders. Shellbags are also recoverable from previous System Restore Points, so you might want to delete those as well. Just run SystemPropertiesProtection.exe and click Configure.
Your antivirus may be responsible for artifacts as well. This study shows that almost all AV programs send browsing data to their servers: http://www.av-comparatives.org/wp-content/uploads/2014/04/avc_datasending_2014_en.pdf. Given that, it seems likely that they would leave logs behind on your machine as well.
Of course, if you take your flash drive to another computer that you cannot control, then you are stuck with these artifacts being left behind.
Other artifacts include the files that could be left behind in the temp file directories specified by the environment variables %TEMP% and %TMP%. However, we have already dealt with these via the rtbaileyphd.com/src/tools/START_PORTABLEAPPS.bat script described above. That script will work even if you take your flash drive to another computer.
Checking for Artifact Leaks Out of Your VeraCrypt Volumes. You can check if registry entries or files are leaking out of your VeraCrypt volumes by using the free Procmon.exe from Microsoft: docs.microsoft.com/en-us/sysinternals/downloads/procmon. Procmon will collect detailed statistics of every registry entry, every file operation, and other I/O events for all processes on your machine. This can be a huge amount of data, so before starting it you should close as many programs and processes on your machine as possible. Also, you will need to set up filters to eliminate showing irrelevant data.
If this person had a hidden volume as described above, he would not be illegally jailed: bleepingcomputer.com/news/legal/man-who-refused-to-decrypt-hard-drives-still-in-prison-after-two-years/. He could have just surrendered his outer volume password and nobody would have been able to prove he had a hidden inner volume.
This page was last modified Thu Mar 07 13:15:06 2019